SAP ERP
Enterprise Resource Planning (ERP)
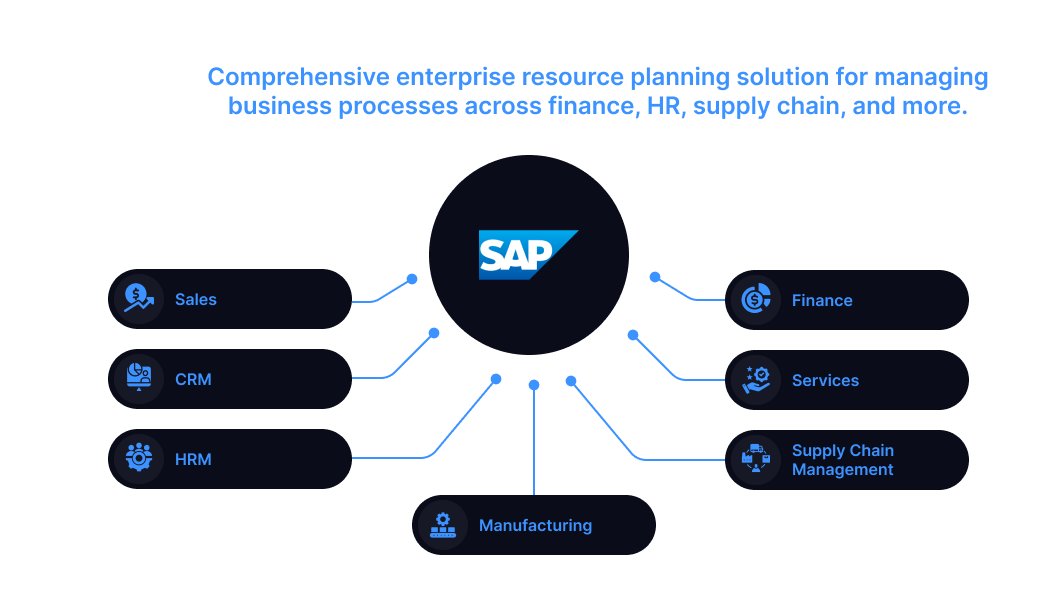
SAP ERP - Comprehensive enterprise resource planning solution for managing business processes across finance, HR, supply chain, and more.
Detection Rules for SAP ERP
These detection rules will focus on various aspects of SAP ERP such as comprehensive enterprise resource planning solution for managing business processes across finance,HR,supply.
Provider: SAP ERP
| Detection Rule | MITRE Tactic | MITRE Technique | Criticality | ||||
|---|---|---|---|---|---|---|---|
| Unauthorized User Access | Initial Access | T1078: Valid Accounts | High | ||||
|
|||||||
| Suspicious Privilege Escalation | Privilege Escalation | T1078.003: Local Accounts | Critical | ||||
|
|||||||
| Data Exfiltration from Financial Records | Exfiltration | T1048: Exfiltration Over Web Service | High | ||||
|
|||||||
| Malicious Payroll Adjustments | Impact | T1485: Data Destruction | High | ||||
|
|||||||
| Unauthorized Vendor Creation | Persistence | T1136.001: Create Account | Medium | ||||
|
|||||||
| Repeated Failed Login Attempts | Credential Access | T1110: Brute Force | High | ||||
|
|||||||
| Unauthorized Data Access in HR Records | Credential Access | T1078: Valid Accounts | High | ||||
|
|||||||
| Large-Scale Data Export Requests | Exfiltration | T1030: Data Transfer Size Limits | High | ||||
|
|||||||
| Manipulation of Inventory Data | Impact | T1485: Data Destruction | Medium | ||||
|
|||||||
| Network Access from Suspicious IP | Command and Control | T1071.001: Web Protocols | High | ||||
|
|||||||
| System Configuration Changes | Defense Evasion | T1070.003: Clear Command History | Medium | ||||
|
|||||||
| Suspicious Changes to Financial Settings | Impact | T1484.001: Domain Policy Modification | High | ||||
|
|||||||
| Unexpected System Process Spawning | Execution | T1059: Command and Scripting Interpreter | High | ||||
|
|||||||
| Bulk User Account Lockouts | Credential Access | T1110.001: Account Lockouts | Medium | ||||
|
|||||||
| Abnormal Export of Client Data | Collection | T1530: Data from Cloud Storage Object | High | ||||
|
|||||||
APIs and Their Scopes
| App : Sap | Required API | Scopes Required | Usage |
|---|---|---|---|
| Unauthorized User Access | SAP Identity Authentication API | Read: User Events | Retrieve logs on user login events to detect unauthorized or unusual access patterns. |
| Suspicious Privilege Escalation | SAP User Management API | Read: User Role Changes | Monitor user privilege modifications to detect unauthorized role escalations. |
| Data Exfiltration from Financial Records | SAP Audit Logging API | Read: Financial Data Access Logs | Track export and data access events within financial modules to detect large or unusual data movements. |
| Malicious Payroll Adjustments | SAP Payroll API | Read: Financial Data Access Logs | Review payroll modification events for suspicious changes. |
| Unauthorized Vendor Creation | SAP Procurement API | Read: Vendor Creation Logs | Track vendor creation logs for actions performed by unauthorized users. |
| Suspicious Purchase Order Modifications | SAP Purchase Order API | Read: Order Modification Logs | Monitor purchase order changes to detect unauthorized modifications. |
| Repeated Failed Login Attempts | SAP Identity Authentication API | Read: Failed Login Events | Retrieve records of failed login attempts to identify potential brute-force or credential-stuffing attacks. |
| Unauthorized Data Access in HR Records | SAP HR Management API | Read: HR Data Access | Monitor access logs for HR data to detect unauthorized access. |
| Large-Scale Data Export Requests | SAP Data Export API | Read: Export Request Logs | Review large or repeated data export requests for potential data exfiltration. |
| Network Access from Suspicious IP | SAP Network Access API | Read: Access Location Data | Retrieve IP addresses used in logins and activity to verify location and legitimacy. |
| System Configuration Changes | SAP System Configuration API | Read: Configuration Changes | Track system configuration changes to detect unauthorized alterations. |
| Suspicious Changes to Financial Settings | SAP Financial Settings API | Read: Settings Change Logs | Review changes to financial settings for unauthorized modifications. |
| Unexpected System Process Spawning | SAP System Process Monitoring API | Read: Process Spawn Events | Track unusual processes initiated within the SAP ERP environment. |
| Bulk User Account Lockouts | SAP Identity Management API | Read: Account Lockout Events | Review events related to multiple user account lockouts to identify potential brute-force attacks. |
| Abnormal Export of Client Data | SAP Data Export API | Read: Sensitive Data Export | Monitor exports of sensitive client data to detect unusual or unauthorized access patterns. |
Reports and Widgets for CISO
| Report Name | Widgets | Description |
|---|---|---|
| User Access and Authentication | Failed Login Attempts Line graph | Tracks login activity to detect unauthorized access attempts and geographic anomalies in login behavior. |
|
Successful vs. Failed Logins Pie chart Geo-Location Login Map World Map |
||
| Privilege Escalation Monitoring | Recent Role Changes List view with user and role details | Identifies and highlights unusual role changes, helping detect unauthorized privilege escalations. |
|
Top Privilege Escalations Bar chart by role type Anomalous Role Changes Indicator |
||
| Data Exfiltration Activity | Export Volume by Module Stacked bar chart | Monitors data export activity for potential data exfiltration incidents, especially in sensitive modules. |
|
Top Data Accessed (table) Unusual Data Access Events (alert indicators) |
||
| Payroll and Financial Integrity | Payroll Modification Events Timeline | Tracks payroll and financial changes, alerting on potential fraud or unauthorized modifications. |
|
Transaction Volume by User Heatmap Unusual Financial Transactions Alert indicators |
||
| Vendor Management and Procurement | New Vendors Created List view with user details | Monitors procurement activity, flagging unusual vendor creation or adjustments to detect fraud. |
|
Top Supplier Adjustments Bar chart Unusual Procurement Activity Alert indicators |
||
| System Configuration and Integrity | Configuration Change Log Log view with timestamps | Tracks changes in system configurations to identify unauthorized modifications to critical settings. |
|
System Alerts Alert panel Unauthorized Configuration Changes Indicator |
||
| Inventory Management Integrity | Inventory Changes Table with item details | Monitors inventory changes for potential tampering or unauthorized adjustments. |
|
Top Inventory Modifiers Bar chart Suspicious Inventory Adjustments Alert indicators |
||
| Network Activity | Access by IP Location Map | Analyzes network access to detect login attempts from suspicious IP addresses or regions. |
|
Network Access Attempts Line graph Suspicious IP Login Events Alert indicators |
||
| Incident Response Overview | Incident Status by Type Pie chart | Provides an overview of incident management, helping CISOs track ongoing investigations and resolution times. |
|
Average Time to Resolution Gauge Open Security Incidents List with priority levels |