Zscaler
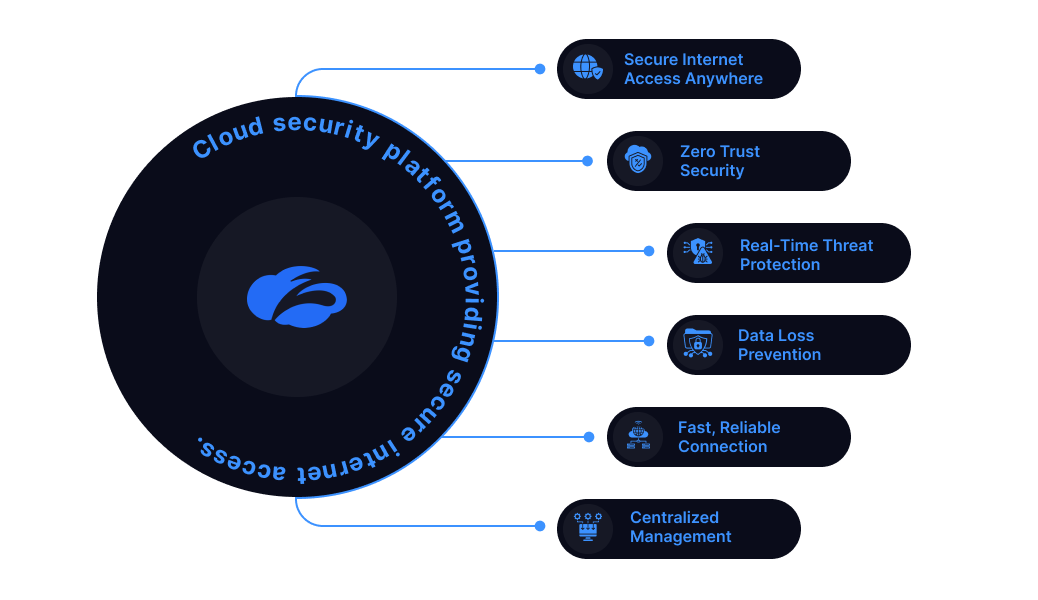
Zscaler - Cloud security platform providing secure internet access.
Detection Rules for Zscaler
These detection rules will focus on various aspects of Workday such as cloud based HR & finance software for workforce management.
Provider: Zscaler
| App : Zscaler | MITRE Tactic | MITRE Technique | Criticality | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Unusual Data Transfer | Exfiltration | T1041: Exfiltration Over Command and Control Channel | High | ||||||
|
|||||||||
| Malicious URL Access | Command and Control | T1071: Application Layer Protocol | High | ||||||
|
|||||||||
| Anomalous User Behavior | Initial Access | T1078: Valid Accounts | High | ||||||
|
|||||||||
| Shadow IT Detection | External Remote Services | T1135: Accessing Remote Services | Medium | ||||||
|
|||||||||
| SSL Inspection Bypass Attempts | Discovery | T1083: File and Directory Discovery | Medium | ||||||
|
|||||||||
| Unauthorized Access to Sensitive Resources | Credential Access | T1078: Valid Accounts | High | ||||||
|
|||||||||
| Insider Threat Indicators | Execution | T1086: PowerShell | High | ||||||
|
|||||||||
APIs and Their Scopes
| App : Zscaler | Required API | Scopes Required | Usage |
|---|---|---|---|
| Unauthorized Access to Patient Records | Workday Audit API | com.workday.audit.patient | To retrieve audit logs on patient record access to identify unauthorized access patterns. |
| Unusual Data Transfer | Zscaler Data Loss Prevention API | Read: DataTransferEvents | To retrieve logs of data transfers to identify sensitive information being transferred outside the organization. |
| Malicious URL Access | URL Threat Intelligence API | Read: URLCategorization | To check if accessed URLs are associated with known malicious activity. |
| Anomalous User Behavior | User Activity Monitoring API | Read: UserLoginEvents | To analyze login attempts and detect unusual patterns across the organization. |
| Shadow IT Detection | Cloud Usage Monitoring API | Read: CloudServiceUsage | To monitor traffic to applications and services not sanctioned by the organization. |
| SSL Inspection Bypass Attempts | SSL Inspection Logs API | Read: SSLInspectionEvents | To analyze attempts to disable SSL inspection and identify potential risks. |
| Unauthorized Access to Sensitive Resources | Access Logs API | Read: SensitiveAccessLogs | To check access logs for unauthorized attempts to sensitive resources and verify user permissions. |
| Insider Threat Indicators | PowerShell Execution Monitoring API | Read: PowerShellExecutionLogs | To analyze PowerShell command execution logs for any suspicious activity indicating potential insider threats. |
Reports and Widgets for CISO
| Report Name | Widgets | Description |
|---|---|---|
| User Activity Report | Top 10 Users by Login Attempts | Summarizes user login activities, including anomalies. |
|
Failed Login Attempts Trend User Login Geographic Distribution |
||
| Malicious URL Access Report | Top Blocked Malicious URLs | Identifies attempts to access known malicious URLs. |
|
Daily Malicious URL Access User Activity on Blocked URLs |
||
| Data Loss Prevention Report | Data Transfer Attempts Overview | Analyzes potential data exfiltration incidents. |
|
Blocked Data Transfers by User Sensitive Data Access Attempts |
||
| SSL Inspection Report | SSL Inspection Bypass Events | Evaluates SSL traffic and any bypass attempts. |
|
SSL Inspection Success Rate Impact of SSL Traffic on Security Events |
||
| Shadow IT Report | Top Unsanctioned Applications Used | Detects unauthorized application usage. |
|
User Access to Shadow IT Services Volume of Traffic to Unsanctioned Apps |
||
| Insider Threat Report | Unusual PowerShell Execution Attempts | Monitors for signs of insider threats through activity. |
|
Unauthorized Access Events Trends in Suspicious User Behavior |
||
| Network Security Events Report | Security Alerts Overview | Aggregates security events, including alerts and incidents. |
|
Incident Response Status Top 10 Security Events by Severity |