Microsoft SharePoint
Communication and Collaboration
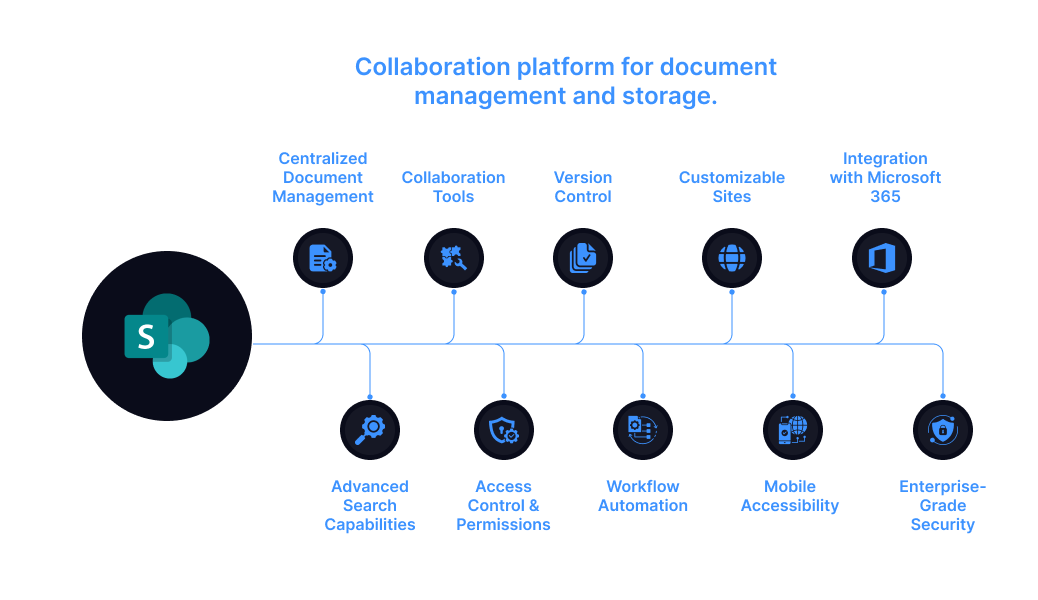
Microsoft SharePoint - Collaboration platform for document management and storage.
Detection Rules for Microsoft SharePoint
These detection rules for Microsoft SharePoint will focus on monitoring potential security threats related to document management and collaboration, ensuring the integrity and confidentiality of sensitive information. By identifying unauthorized access, data exfiltration attempts, and suspicious user activities, these rules help safeguard the platform against emerging security risks.
Provider: Microsoft SharePoint
| Detection Rule | MITRE Tactic | MITRE Technique | Criticality | ||||
|---|---|---|---|---|---|---|---|
| Unauthorized Access to SharePoint Files | Credential Access | T1078 - Valid Accounts | High | ||||
|
|||||||
| File Exfiltration via SharePoint | Exfiltration | T1048 - Exfiltration Over Web Service | Critical | ||||
|
|||||||
| Privilege Escalation on SharePoint | Privilege Escalation | T1078.003 - Valid Accounts: Cloud Accounts | High | ||||
|
|||||||
| Suspicious File Sharing | Command and Control | T1071.001 - Application Layer Protocol: Web Protocols | Medium | ||||
|
|||||||
| Abnormal File Upload Activity | Exfiltration | T1071.001 - Application Layer Protocol: Web Protocols | High | ||||
|
|||||||
| SharePoint Account Compromise | Initial Access | T1078.003 - Valid Accounts: Cloud Accounts | Critical | ||||
|
|||||||
| Document Deletion or Tampering | Impact | T1485 - Data Destruction | High | ||||
|
|||||||
| External Sharing of Sensitive Data | Exfiltration | T1071.001 - Application Layer Protocol: Web Protocols | High | ||||
|
|||||||
| Mass File Download | Collection | T1071.001 - Application Layer Protocol: Web Protocols | Medium | ||||
|
|||||||
| File Integrity Monitoring (FIM) Anomalies | Impact | T1496 - Resource Hijacking | Medium | ||||
|
|||||||
| Anonymous Access to SharePoint Files | Collection | T1530 - Data from Cloud Storage Object | Critical | ||||
|
|||||||
APIs and Their Scopes
| Detections Name | API Required | Scope Required | Usage |
|---|---|---|---|
| Unauthorized Access to SharePoint Files | Microsoft Graph API | AuditLog.Read.All | Access audit logs to review user access history, identify unauthorized access to files, and check login behavior. |
| File Exfiltration via SharePoint | Microsoft Graph API | Files.Read, AuditLog.Read.All | Review file download logs and monitor exfiltration attempts via SharePoint. |
| Privilege Escalation on SharePoint | Microsoft Graph API | Directory.Read.All | Analyze role changes and privilege escalations for suspicious activity. |
| Suspicious File Sharing | Microsoft Graph API | Sites.Read.All, AuditLog.Read.All | Review external file sharing and analyze if any sensitive documents were shared with unauthorized users. |
| Abnormal File Upload Activity | Microsoft Graph API | Sites.ReadWrite.All | Monitor large or unusual file uploads, especially to external locations. |
| SharePoint Account Compromise | Azure AD API, VirusTotal API | SignIns.Read.All, VirusTotal API Key | Check account login behavior via Azure AD, analyze suspicious IP addresses with VirusTotal to confirm account compromise. |
| Document Deletion or Tampering | Microsoft Graph API, File Integrity APIs | AuditLog.Read.All | Access logs for document deletion or tampering, verify with file integrity monitoring APIs for unauthorized changes. |
| External Sharing of Sensitive Data | Microsoft Graph API | AuditLog.Read.All, Sites.Read.All | Review external file sharing of sensitive documents and monitor for unauthorized sharing events. |
| Mass File Download | Microsoft Graph API | Sites.Read.All, AuditLog.Read.All | Monitor large file downloads and analyze download patterns, especially from sensitive or confidential folders. |
| File Integrity Monitoring (FIM) Anomalies | File Integrity Monitoring (FIM) APIs | Depends on FIM provider | Monitor file integrity changes, detect anomalies, and identify unauthorized modifications to critical files. |
| Anonymous Access to SharePoint Files | Microsoft Graph API | AuditLog.Read.All, Sites.Read.All | Track and analyze anonymous access attempts to sensitive SharePoint files or folders. |
Reports and Widgets for CISO
| Report Name | Widgets | Description |
|---|---|---|
| Unauthorized Access Report | Heatmap: Access by User | Monitor and track unauthorized access attempts to SharePoint sites and documents, highlighting potential insider threats. |
|
Bar Chat: Unauthorized Access Attempt Summary Map View: Geo-location of Access |
||
| Privilege Escalation Report | Timeline View: Privilege Changes by User | Track and monitor changes in user privileges and roles, identifying any abnormal or unauthorized privilege escalations. |
|
Stacked Bar Chart: Role Changes Pie Chart: Admin Account Usage |
||
| Suspicious File Sharing Report | Pie Chart: External File Shares | Review external file sharing events, especially with sensitive data or suspicious links being shared externally. |
|
Highlighted Table: Sensitive File Sharing Shared Links to External Domains |
||
| Abnormal File Upload Activity Report | Line Graph: File Uploads by Size | Detect abnormal file upload activity to critical or sensitive SharePoint folders, focusing on file size and volume. |
|
Bar Chart: User Upload Patterns Highlight: Sensitive Folders Upload Activity |
||
| Account Compromise Report | Map View: Account Logins by Geo-location | Identify compromised accounts by tracking anomalous login behavior, unusual geo-locations, and abnormal success/failure rates. |
|
Line Graph: Anomalous Login Attempts Donut Chart: Login Success Rate |
||
| Document Deletion and Tampering Report | Bar Chart: Document Deletions by User | Track document deletions and unauthorized tampering, with options for seeing restored versions or previous versions. |
|
Table: Tampered Documents Line Graph: Restoration History |
||
| External Sharing of Sensitive Data Report | Highlighted Table: External Sharing of Confidential Files | Focus on external sharing of sensitive or confidential data, including tracking who shared, what was shared, and with whom. |
|
Bar Chart: Sharing by Domain Activity Log: Shared Links Activity |
||
| Mass File Download Report | Heatmap: File Downloads by User | Analyze and identify mass file downloads that may indicate data theft or improper usage of corporate data. |
|
Line Graph: Download Volume by Time Leaderboard: Top Downloaders |
||
| File Integrity Monitoring (FIM) Anomalies Report | Timeline View: File Changes | Detect anomalies in file integrity, such as unauthorized modifications or violations of security policies on critical files. |
|
Heatmap: Integrity Violations Highlighted Table: File Recovery Attempts |
||
| Anonymous Access to Files Report | Stacked Bar Chart: Anonymous File Access Attempts | Monitor attempts to access SharePoint files anonymously, including identifying the most accessed documents and source IPs. |
|
List with Timestamps: Most Accessed Documents Access by IP |
||
| Audit Log Summary Report | Bar Chart: Access Logs by User | Provide a summary of overall SharePoint activities, including user access logs, activities, and identifying potential anomalies. |
|
Line Graph: Activity by Time Highlighted Table: Anomalous Events |
||
| Compliance Monitoring Report | Pie Chart: Sensitive Data Access | Ensure that SharePoint data handling complies with regulatory standards, focusing on sensitive data access and violations. |
|
Highlighted Table: Regulatory Violations Bar Chart: Data Retention Violations |